Defending Against APTs: How to Protect Against a Silent Threat
20 Strategies to Prevent Cyber Attacks Driven by Advanced Persistent Threats
Advanced Persistent Threats (APTs) are among the most sophisticated and damaging forms of cyber attacks faced by organizations today. These highly targeted, well-funded, and persistent attacks aim to gain unauthorized access to a network and remain undetected for extended periods. Their primary goal often involves stealing sensitive data, compromising intellectual property, or sabotaging critical systems. To defend against these threats effectively, organizations need to adopt a proactive and comprehensive security posture.
Understanding the Anatomy of an APT
An Advanced Persistent Threat (APT) represents a highly targeted and calculated cyber attack, distinct in its methodology and longevity. These attacks are often orchestrated by well-funded entities, aiming to achieve long-term objectives such as espionage, data theft, or disruption. APTs unfold across distinct stages, each demanding specific defenses to mitigate the impact.
The first stage, reconnaissance, involves gathering critical information about the target organization. This may include mapping network architecture, identifying key personnel, and probing for vulnerabilities. Attackers often leverage open-source intelligence (OSINT) and social engineering during this phase.
Initial compromise follows, employing methods such as spear-phishing emails, zero-day exploits, or malicious supply chain infiltrations. The goal is to establish a foothold within the network by exploiting vulnerabilities or deceiving users into executing malicious payloads.
Once inside, the attackers work on establishing persistence. They deploy backdoors, malware, or use stolen credentials to ensure ongoing access. This stage often goes unnoticed as attackers focus on blending into the network’s normal activity.
During the lateral movement phase, attackers explore the internal network, escalating privileges and accessing sensitive assets. Techniques like pass-the-hash and credential dumping are frequently used to bypass security controls.
Finally, the attack culminates in exfiltration or sabotage. Critical data is extracted, or systems are disrupted to fulfill the attackers’ goals. This stage often reveals the attack but typically occurs after significant damage has been done.
Key Strategies to Mitigate APT Risks
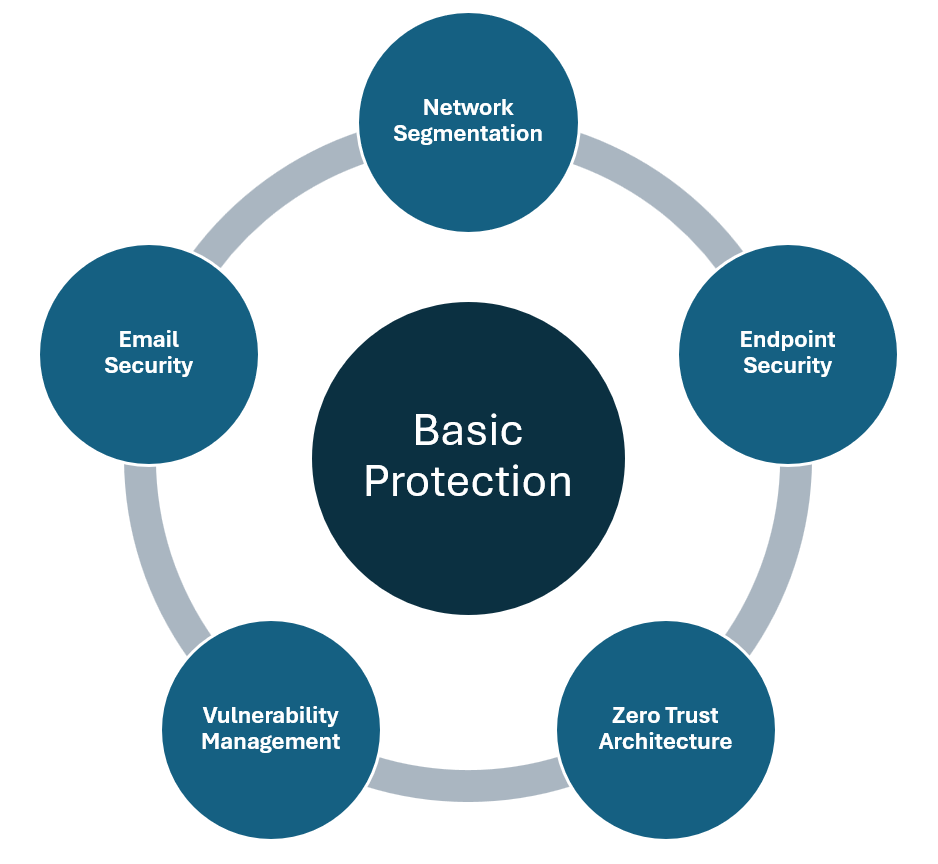
Defending against Advanced Persistent Threats (APTs) requires a strategic approach that integrates robust technologies, strong processes, and informed personnel. APTs are persistent and well-resourced, making layered defenses essential for minimizing vulnerabilities. Below are key strategies to mitigate APT risks effectively.
1. Implement Network Segmentation
Network segmentation confines attackers to limited portions of a network, hindering their ability to explore and exploit. By dividing a network into zones based on business functions or sensitivity levels, organizations create boundaries that reduce risk. Firewalls and access controls enforce these divisions, while isolating critical systems ensures that high-value targets are shielded from less secure areas.
2. Enhance Endpoint Security
Endpoints, such as laptops and mobile devices, are frequent targets for APT entry. Deploying advanced endpoint protection tools enables detection of malware, exploitation attempts, and anomalous behavior. Endpoint Detection and Response (EDR) solutions add an additional layer by providing continuous monitoring and enabling swift responses to threats.
3. Adopt a Zero Trust Architecture
Zero Trust principles operate under the assumption that no user or device can be trusted without verification. By enforcing multifactor authentication (MFA), implementing least-privilege access controls, and continuously validating access requests, organizations significantly reduce the chances of unauthorized access. This approach minimizes the risk posed by compromised credentials or insider threats.
4. Conduct Regular Vulnerability Management
Unpatched vulnerabilities are a common entry point for APTs. Regular vulnerability scans identify weak points in the network, while automated patch management ensures prompt resolution. By prioritizing high-risk vulnerabilities, organizations can proactively close gaps before attackers exploit them.
5. Strengthen Email Security
Spear-phishing remains a favored method for initiating APTs. Email filtering solutions can block phishing attempts before they reach users, while employee training fosters awareness of how to spot and report suspicious emails. This combination reduces the likelihood of attackers gaining initial access.
While integrating these measures supports any organization to build a robust defense against APTs, it is barely the minimum you can do to safeguard effectively against APTs. As outlined earlier, APTs are usually well-funded and resourceful entities, often sponsored by nation states. These resources are used to overcome basic security mechanisms. To effectively counter Advanced Persistent Threats, organizations must integrate advanced detection tools, robust response mechanisms, and a proactive security culture additionally.
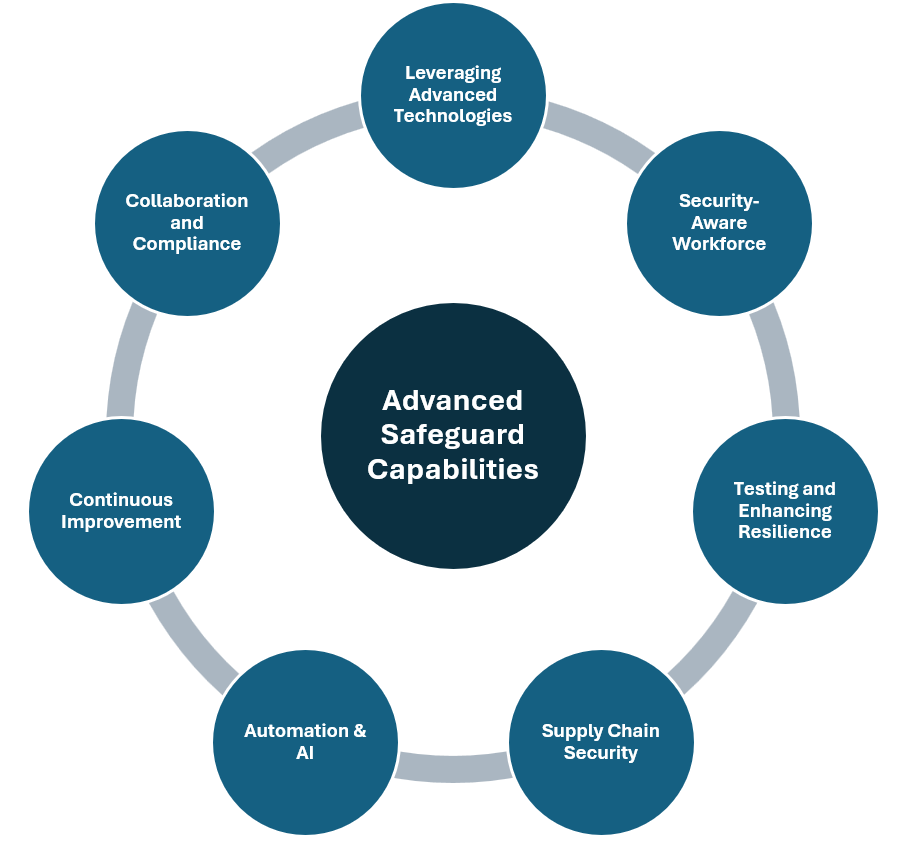
Advanced Safeguard Capabilities to Effectivley Protect Against APTs
The following strategies offer a comprehensive approach to detecting and mitigating these sophisticated attacks.
Leveraging Advanced Technologies
6. Use Threat Intelligence: Staying informed about emerging threats allows organizations to anticipate and prepare for potential attacks. By subscribing to threat intelligence feeds and collaborating with industry peers, security teams can fine-tune their controls and identify evolving attack patterns.
7. Deploy Security Information and Event Management (SIEM) Systems: SIEM systems centralize network visibility by collecting and analyzing logs across systems. Paired with User and Entity Behavior Analytics (UEBA), SIEM identifies unusual patterns, enabling swift action against anomalies.
8. Integrate Extended Detection and Response (XDR): XDR consolidates data from multiple sources—endpoints, network traffic, and applications—to detect intricate attack chains. Automating responses minimizes the time attackers have to exploit vulnerabilities.
Building a Security-Aware Workforce
9. Conduct Regular Training: Employees often serve as the first line of defense. Ongoing training, tailored to job roles, raises awareness about safe practices and equips employees to recognize threats like phishing attempts. Simulated exercises reinforce this knowledge.
10. Establish an Incident Reporting Culture: Encouraging employees to report suspicious activities without fear fosters quick threat identification. Simple, accessible reporting mechanisms ensure that potential issues are addressed promptly.
Testing and Enhancing Resilience
11. Perform Red Team Exercises: Simulating APT attacks helps identify vulnerabilities within defenses. Insights from these tests inform improvements in detection and response mechanisms.
12. Regularly Test Incident Response Plans: Conducting tabletop exercises and live simulations prepares teams for real-world scenarios. Continuous updates to response plans ensure readiness for evolving threats.
Securing the Supply Chain
13. Assess Vendor Security: Third-party vendors often represent weak links. Conducting thorough security evaluations ensures that partners comply with stringent cybersecurity standards.
14. Monitor Supply Chain Risks: Attackers frequently exploit vulnerabilities in supply chains. Monitoring tools and contractual obligations for breach notifications strengthen this critical area.
Harnessing Automation and AI
15. Automate Threat Detection: Machine learning algorithms detect anomalies faster and more accurately than manual methods. Automating repetitive tasks, such as log analysis, frees resources for strategic initiatives.
16. Employ Deception Technologies: Decoys and honeypots mislead attackers, delaying their progress and providing valuable intelligence about their tactics and techniques.
Continuous Improvement
17. Engage in Threat Hunting: Dedicated teams proactively search for indicators of compromise (IoCs) and anomalous activities that might bypass standard controls.
18. Use Post-Incident Analysis: Analyzing past incidents reveals weaknesses exploited by attackers. Findings are critical for strengthening defenses and preventing future breaches.
Collaboration and Compliance
19. Collaborate with External Partners: Sharing intelligence with industry groups and governmental bodies enhances threat awareness. Participation in threat-sharing platforms ensures up-to-date defenses.
20. Ensure Regulatory Compliance: Aligning with standards like NIST or ISO 27001 reinforces security practices. Regular audits address gaps and ensure adherence to evolving regulatory demands.
Closing Thoughts
Advanced Persistent Threats (APTs) are a serious challenge, but organizations can minimize their exposure with proactive efforts and a layered security approach. Leveraging advanced technologies like behavioral analytics, machine learning, and zero-trust frameworks helps detect and mitigate threats more effectively. Regularly updating and patching systems reduces vulnerabilities that attackers might exploit.
Equally crucial is fostering a strong security culture across the organization. Employees need ongoing education to recognize phishing attempts, avoid risky behavior, and report suspicious activity. Clear policies and a supportive environment encourage staff to remain vigilant against potential threats.
Continuous monitoring of networks and systems ensures rapid detection and response to malicious activity. Threat intelligence sharing with industry peers and utilizing external expertise can provide valuable insights into emerging risks and tactics used by attackers.
An effective strategy involves blending robust technical defenses with human awareness and preparation. Organizations that demonstrate such resilience become less appealing to adversaries seeking easier targets. To effectively protect critical assets from advanced persistent threats and sophisticated cyber attacks, companies must remain vigilant and adaptable. Are your defenses ready to face the evolving challenges of today's cybersecurity landscape?