The NotPetya Cyber Attack
From Cyber Crime to Cyber War
Ukraine, June 2017.
A devastating cyber attack known as NotPetya struck, initially targeting the country but quickly spreading globally.
This malware, masquerading as ransomware, was designed to cause maximum disruption rather than financial gain. It leveraged vulnerabilities in Windows systems, exploiting tools like EternalBlue and Mimikatz.
The Attack
The attack began on June 27, 2017, using a compromised Ukrainian accounting software, M.E.Doc, as the initial infection vector. Once inside a network, NotPetya spread rapidly, encrypting files and the master boot record, rendering systems inoperable. Unlike typical ransomware, paying the ransom did not guarantee data recovery, highlighting its destructive intent.
NotPetya combined several sophisticated techniques to maximize its impact. The malware initially spread through a software update mechanism of M.E.Doc, a popular accounting software in Ukraine. This update contained a backdoor that allowed the attackers to execute the malware on the infected systems.
Once deployed, NotPetya used multiple methods to propagate within networks:
EternalBlue Exploit: This exploit targeted a vulnerability in the SMBv1 protocol of Windows systems, allowing the malware to spread without user interaction.
Credential Theft: NotPetya used a modified version of the Mimikatz tool to steal credentials from the infected system’s memory. These credentials were then used to move laterally across the network.
PsExec and WMI: The malware also utilized legitimate Windows tools like PsExec and Windows Management Instrumentation (WMI) to execute commands on remote systems.
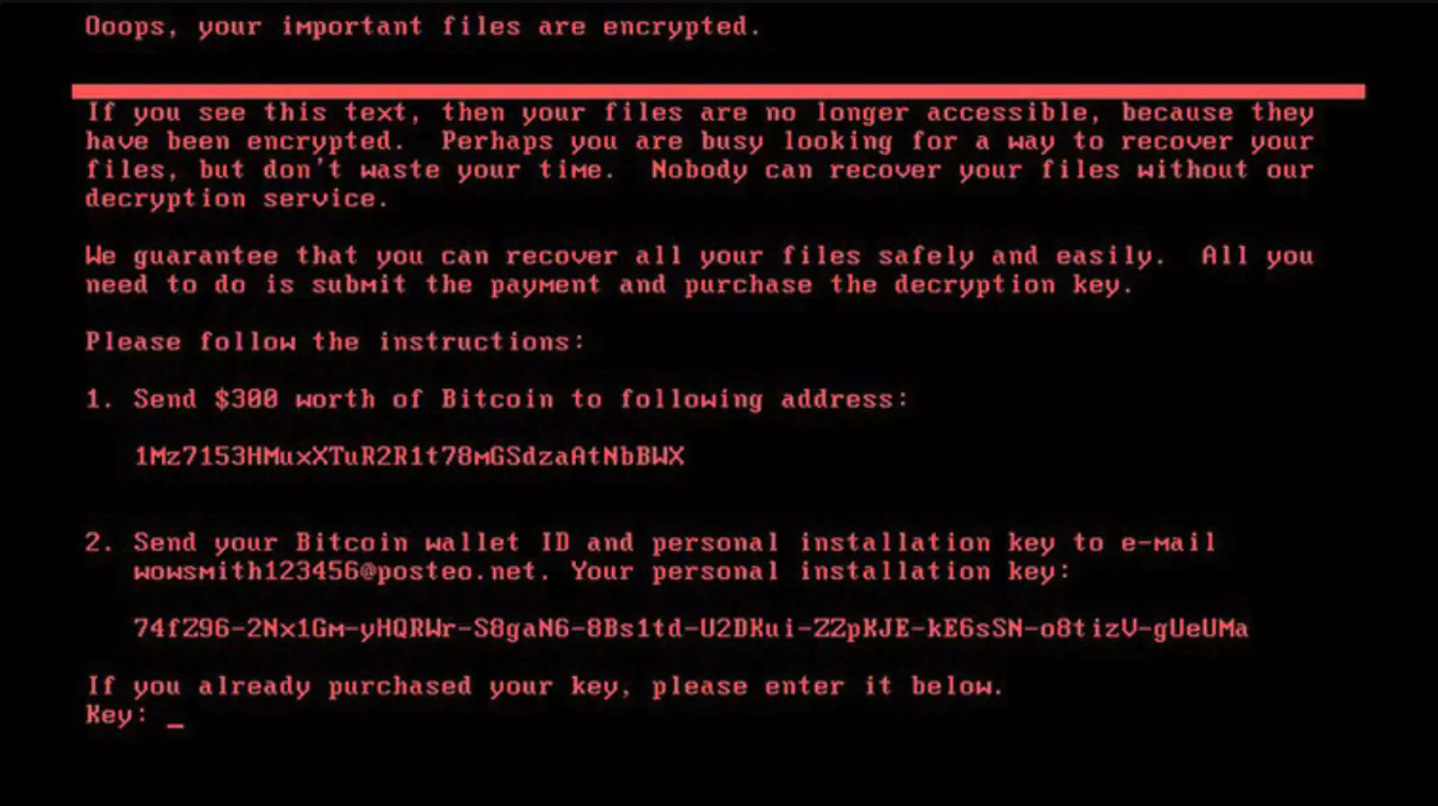
The malware’s payload included File Encryption where NotPetya encrypted files on the infected systems, making them inaccessible. It also encrypted the Master Boot Record (MBR), preventing the system from booting. Lastly, it created a false ransom note, demanding $300 in Bitcoin. However, paying the ransom did not result in data recovery.
Attack Response
Organizations affected by NotPetya scrambled to contain the spread. Immediate responses included isolating infected systems, shutting down networks, and restoring from backups where possible. Governments and cybersecurity firms provided support, sharing indicators of compromise and mitigation strategies.
The response to NotPetya involved several critical steps:
Isolation: Infected systems were quickly isolated from the network to prevent further spread.
Shutdown: Some organizations opted to shut down their entire network infrastructure to halt the malware’s propagation.
Restoration from Backups: Companies with robust backup systems were able to restore their data and resume operations more quickly.
Collaboration and Information Sharing: Governments and cybersecurity firms collaborated to share information about the malware and effective mitigation strategies.
For example, Maersk, a major global shipping company, had to rebuild its entire IT infrastructure from scratch. The company set up an emergency recovery center in the UK and worked around the clock to restore operations. This effort involved hundreds of staff members and took several weeks to complete.
Impact to the Victim and Other Stakeholders
NotPetya caused widespread disruption, affecting major companies like Maersk, Merck, and FedEx. The financial impact was staggering, with estimated damages exceeding $10 billion. Beyond financial losses, the attack highlighted vulnerabilities in global supply chains and the interconnected nature of modern business operations.
Maersk: The shipping giant temporarily lost access to its entire global network, affecting operations at 76 ports worldwide. The company had to reinstall 4,000 servers, 45,000 PCs, and 2,500 applications.
Merck: The pharmaceutical company faced significant disruptions in its manufacturing processes, leading to delays in drug production and distribution.
FedEx: The logistics company experienced severe operational disruptions, particularly in its European subsidiary, TNT Express.
The attack also had broader implications for global cybersecurity. It exposed the vulnerabilities in widely used software and highlighted the need for better security practices and international cooperation in combating cyber threats.
Lessons Learned
The NotPetya attack underscored the importance of robust cybersecurity measures. Key lessons include the need for timely patch management, network segmentation, and comprehensive incident response plans. Organizations also learned the value of collaboration and information sharing in mitigating cyber threats.
What can be learned from this attack?
Patch Management: Ensuring that all systems are up-to-date with the latest security patches is crucial in preventing similar attacks.
Network Segmentation: Dividing the network into smaller segments can limit the spread of malware within an organization.
Incident Response Plans: Having a well-defined incident response plan can help organizations respond more effectively to cyber attacks.
Collaboration: Sharing information about threats and vulnerabilities with other organizations and cybersecurity firms can enhance overall security.
Discussion
a) Knowing how the organization responded, what would you have done differently?
b) What are some steps you think the firm could have taken to prevent this incident?
c) Is your business susceptible? How are you going to reduce your risk?


